Kubernetes Service Account Cluster Role Binding

How to assign cluster role binding to a service account in Kubernetes? How to configure RBAC authorization for a service account in Kubernetes?
Kubernetes uses the Role-based access control (RBAC) method to restrict API access for an account. Under rbac.authorization.k8s.io API group.
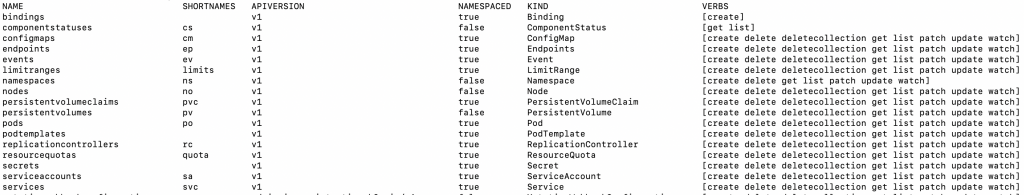
kubectl api-resources -o wide
The command above will get the list of API resources, its name, version, kind and verbs. You will be needing this information when setting the rules for your ClusterRole.

Kubernetes Cluster Role YAML Configuration
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: webapp-secrets-manager
rules:
- apiGroups:
- ""
resources:
- secrets
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]For this tutorial, I am creating a ClusterRole for managing secrets resource.
Kubernetes organize its API endpoints and versioning by related paths. For example, API endpoints that are related to authorization such as ClusterRole and ClusterRoleBinding are under rbac.authorization.k8s.io . That is why, the first line in the above YAML configuration indicates the API group and version apiVersion: rbac.authorization.k8s.io/v1. Another example, Core API endpoints for Service, ServiceAccount and Secret are all under "" (empty string wrapped in double quote). Hence, when defining the version for Core API, it is apiVersion: v1 without any prefix.
I set the name of my ClusterRole “webapp-secrets-manager” under metadata . And rules indicate the following list of configurations.
apiGroups– List of API groups that the resources belongs toresources– Kubernetes resource objects you want to give access toverbs– API resources actions you want to give access to
In this example, I want my ClusterRole to have the ability to manage secrets in my Kubernetes cluster. Therefore, I gave it all needed verbs that includes the permission to add, update, delete and read secrets.
kubectl apply -f k8s-cluster-role.yaml
Then use kubectl apply command to create your ClusterRole.
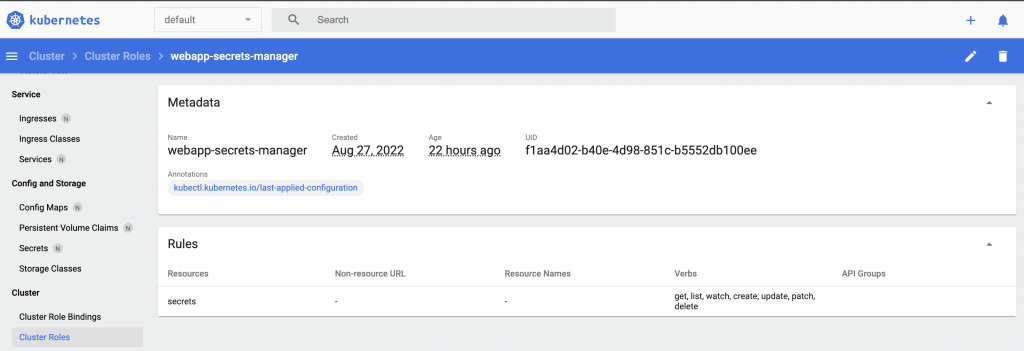
Then if you go to your dashboard, you’ll be able to see your created ClusterRole. The Rules should also match the configuration set in your YAML file.
Service Account and Cluster Role Binding
Now that we have a ClusterRole I want to show how to assign this to a Service Account by defining a Cluster Role Binding.
Kubernetes Service Account YAML Configuration
My goal for this tutorial is to associate permissions to a Service Account. The purpose of a Service Account is to provide an identity for processes that run in a Pod. For example, if I want my Pod (that runs my containerized app) to have access to Kubernetes secrets, I can associate a Service Account to my Pod. Kubernetes cluster, then uses the Service Account to authenticate my Pod.
apiVersion: v1 kind: ServiceAccount metadata: name: webapp-service-account namespace: default
The YAML configuration is simple for this one. The API version is apiVersion: v1. The kind of object resource is ServiceAccount. In metadata, is the name of my ServiceAccount. And it will be created under the default namespace.
Kubernetes Cluster Role Binding YAML Configuration
The last thing we need is the Kubernetes service account cluster role in binding the permission we set for managing the secrets resource.
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: webappp-cluster-role-binding subjects: - kind: ServiceAccount name: webapp-service-account namespace: default roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: webapp-secrets-manager
As I have mentioned earlier, the ClusterRoleBinding object resource is still under rbac.authorization.k8s.io. Therefore, similar to ClusterRole the version is set to apiVersion: rbac.authorization.k8s.io/v1.
My ClusterRoleBinding has three important components. The metadata that has the name attribute, which I set to “webappp-cluster-role-binding”. Second, is the subjects that could be one of users, groups, or service accounts. For this example, it is of a kind ServiceAccount. Moreover, the name of the ServiceAccount is “webapp-service-account”, under “default” namespace. Third, is the roleRef that indicates the details about the ClusterRole we just created.
kubectl apply -f k8s-serviceaccount.yaml kubectl apply -f k8s-cluster-role-binding.yaml
Finally, apply the YAML configurations kubectl apply for both creating a ServiceAccount and ClusterRoleBinding
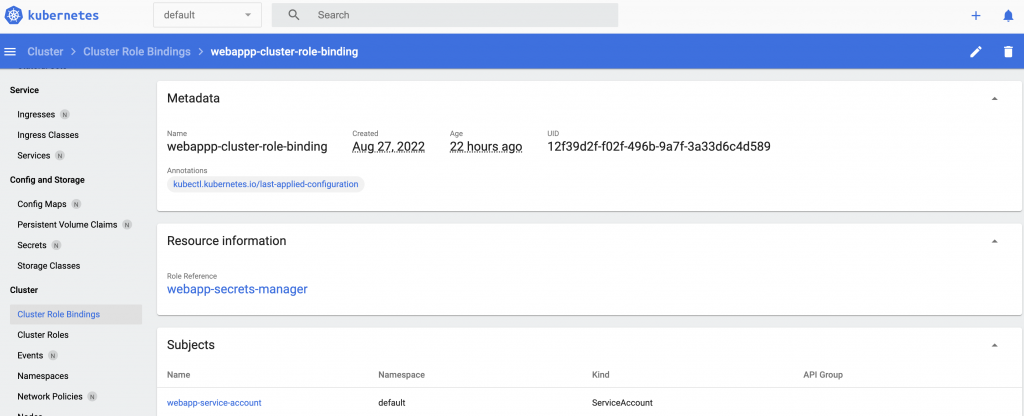
Go to your dashboard, you’ll be able to see the created ClusterRoleBinding and ServiceAccount.