AWS Cognito User Pool

This tutorial is meant for developers who are new to AWS Cognito. This will be a quick topic about AWS Cognito and how to Create a User Pool.
As described in the AWS website, Cognito is a simple and secure user Sign-Up, Sign-In, and Access Control authentication service provided by Amazon. This service allows developers to integrate authentication in their application.
Cognito has many features like Multi-Factor Authentication, hosted UI, OAuth flows and Lambda trigger.
Create a User Pool
Log in to AWS Management Console. If you don’t have an AWS account, you will need to Sign-Up and it’s free to just have an account.
In the Dashboard you will see many AWS services, search for “Cognito”.
Then click on “Manage User Pools”. And along the top right corner, click on “Create a user pool”.

Now you can give your User pool a name, and we will go over the “Step Through Settings”. Take note that after creating the User Pool, you can go back and create changes in the configuration except for the Sign-In and Default attribute options.
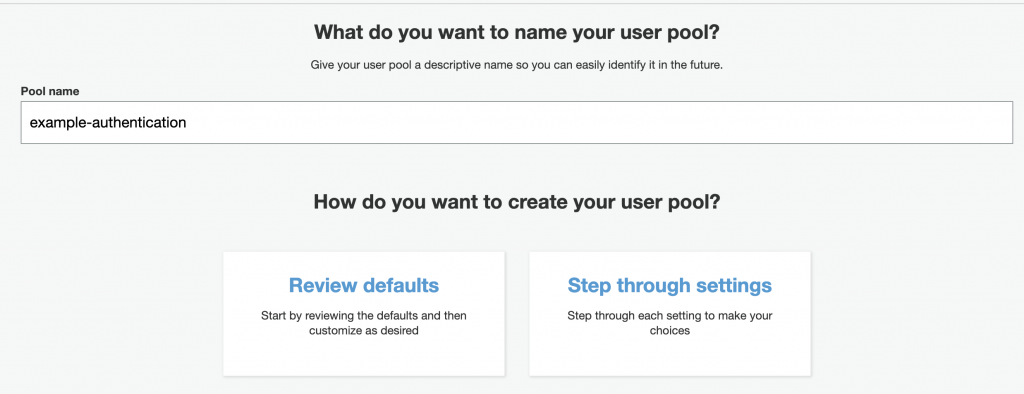
Attributes
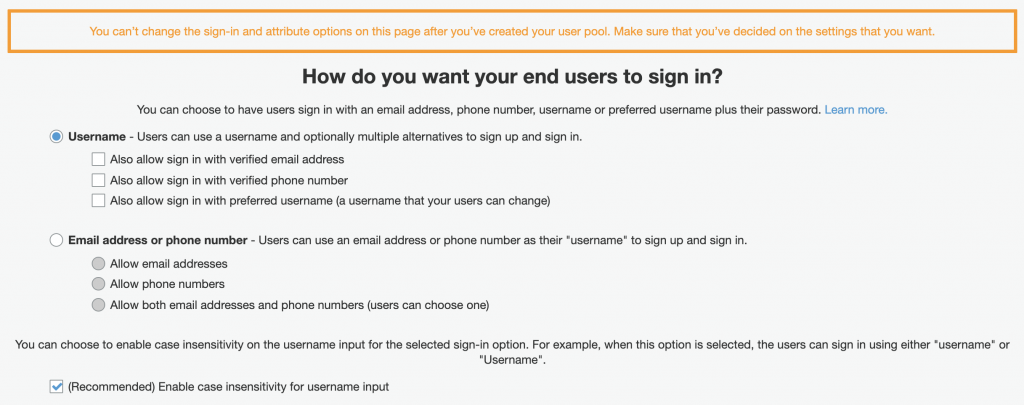
Setup the sign in options. You can select to have users sign in using another attribute in their profile like their email address, phone number, username or preferred username combined with their password. As well, you can make the username case-insensitive.
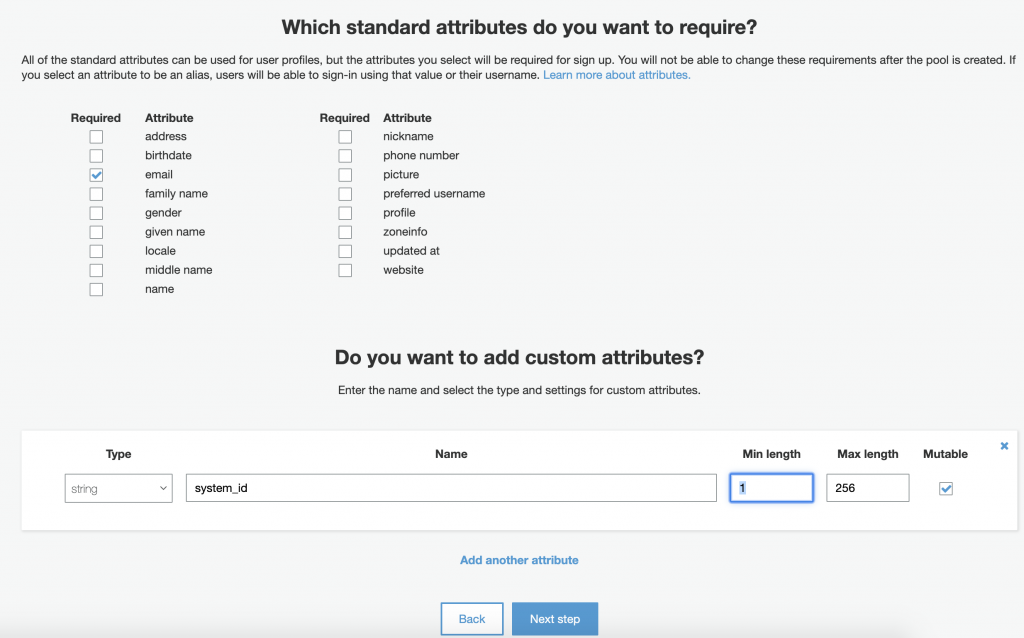
Setup attribute options. This will be the fields in the user profile during sign up. You can also add custom attributes in addition to the defaults that you have chosen.
Policies
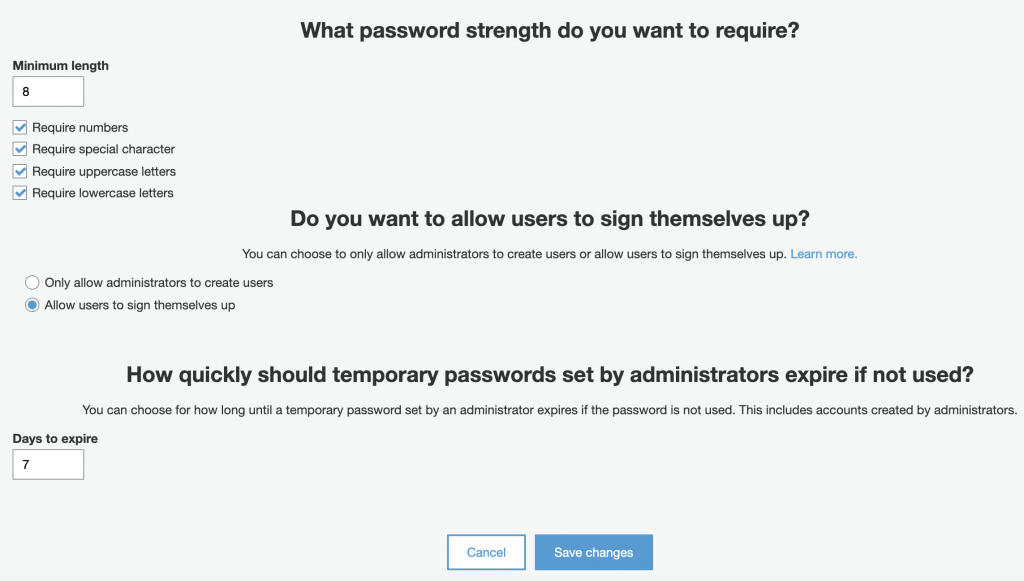
Setup password and Sign-In policy. Apply password requirements such as length, character combination and the lifespan for a temporary password. And for the sign up process if you want to allow a user to create their own account.
MFA and Verification
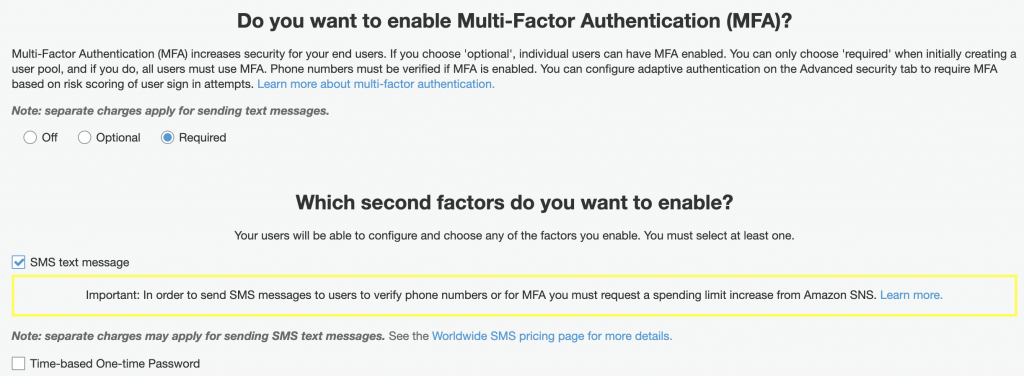
Setup Multi-Factor authentication (MFA), account verification and recovery. MFA is an additional security by having a user use the verification code sent to their email or phone to confirm a sign in to their account. The code must be submitted along with their password to complete the sign in process. You can also disable the feature if not needed.
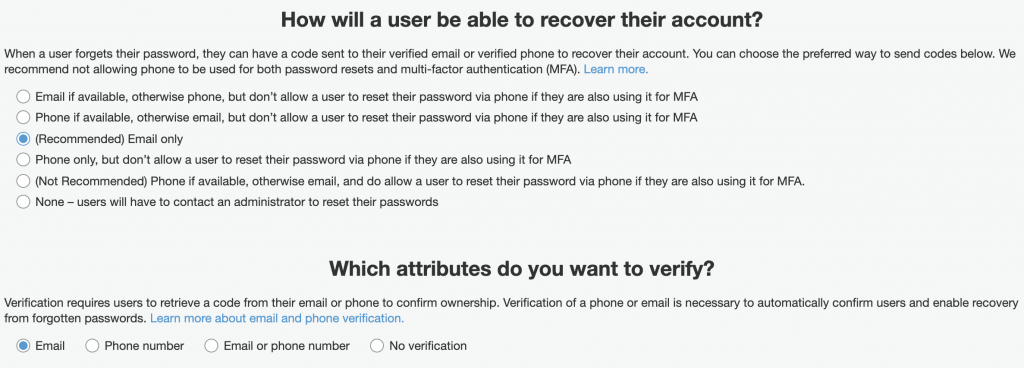
And you can also enable how they can recover their account in the event of forgetting their login credentials.
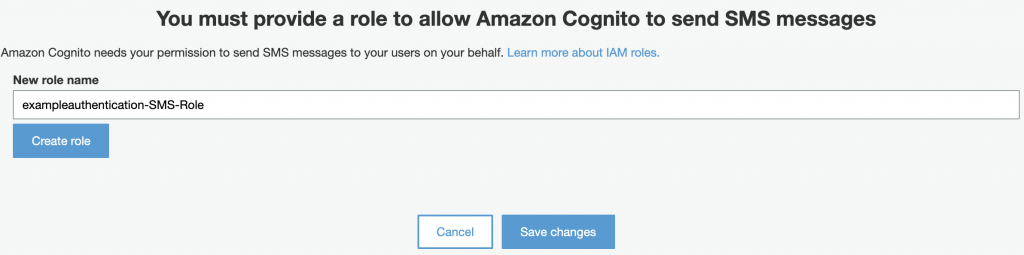
In order to enable SMS messaging, you will need to create an IAM role in your AWS account. If you don’t have one yet, just submit the “Create Role” and it will be automatically created for you.
Message Customization
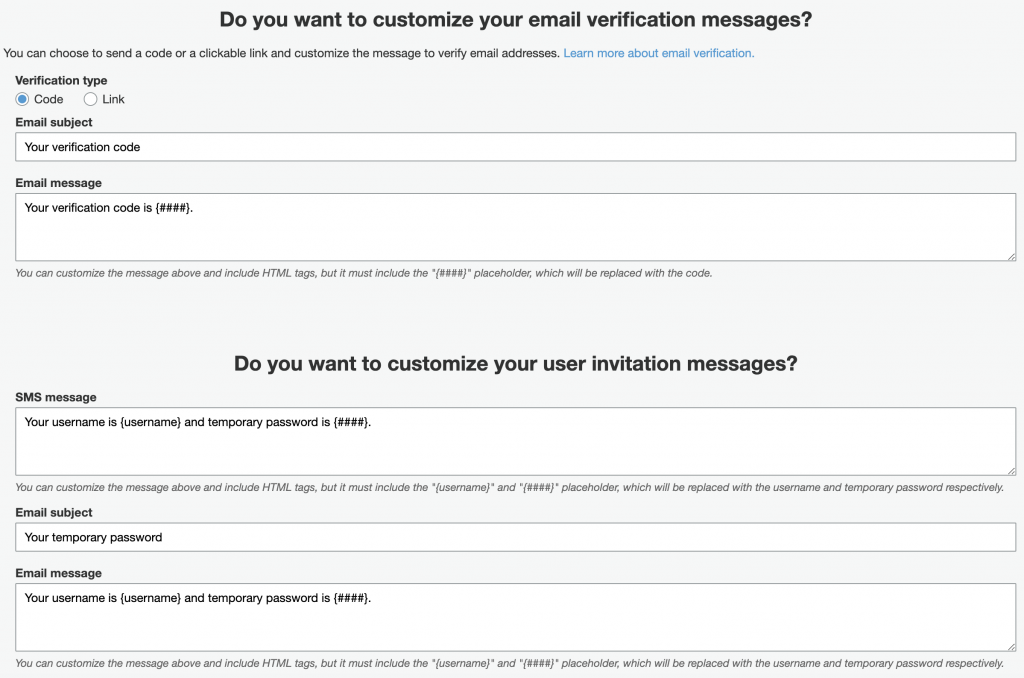
Setup Email Messages and Headers. On this step, you can change the verification and invitation messages for Email and SMS. Also, you can change the email headers for FROM and REPLY-TO in the email.
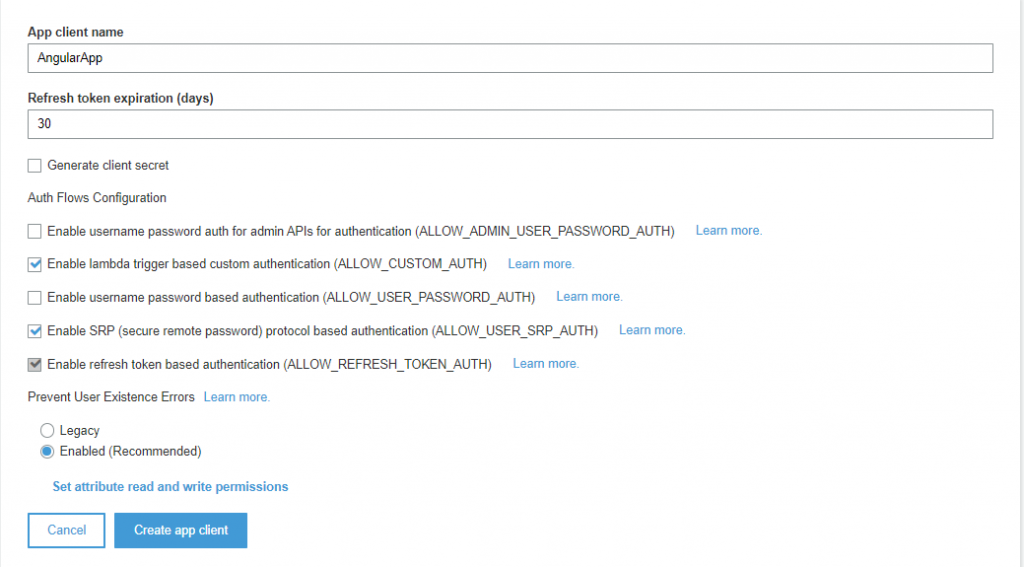
App Clients
This is an important step in setting up an AWS Cognito User Pool. To allow your application (Front-End or Back-End) to access the User Pool, you will need an App Client credential. The App Client will be used to get an Identity Token or Access Token, and then use this in exchange for user profile depending to your authentication flow.
For instance, if you are developing an authentication and sign up module for a Single Page Application (SAP), you can leave most of the default setup checked. And you do not need to generate a Client Secret since this is only for machine to machine authentication.
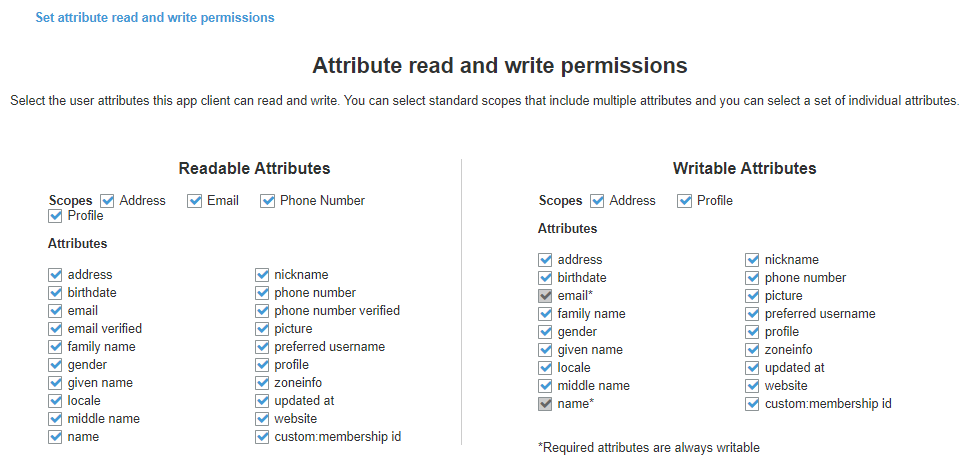
The App Client can also have defined access to the attribute options that has been setup on the early steps.
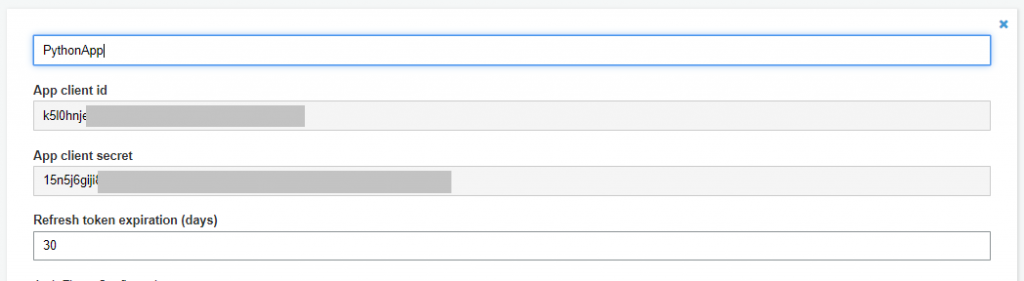
If you are trying to create a Machine to Machine authentication, assuming that the flow will be an OAuth 2.0 Client credential, then the App Client will be the account of the third party Service in your system, having an App client id and App client secret generated.
If you are interested in how to use OAuth 2.0 flows in AWS Cognito, check out my topics about Implicit Flow, Authorization code and Client credentials.
Tags, Devices and Triggers
Setup Pool tags. Tags are useful if you have several AWS Cognito User Pool. Tags can be used to group User Pools per Organization, aggregate billing reports and implement IAM role.
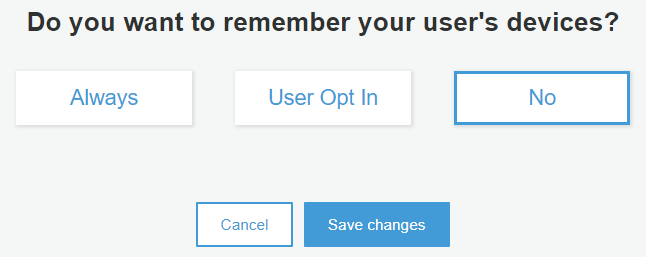
Setup remember device. This is for remembering the device of the user when they sign in. The next time they sign in, they no longer have to confirm again if your application has remembered their device’s identity.
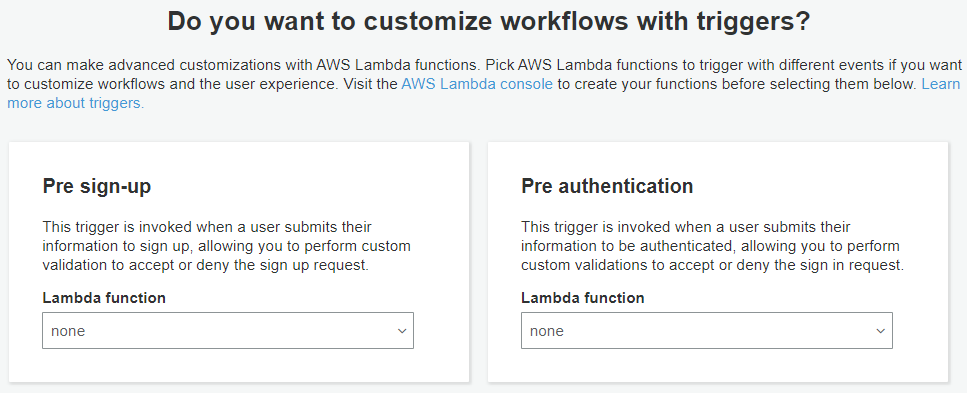
Setup Lambda trigger. One of the useful features of AWS Cognito is the ability to trigger a lambda function based on events. This is applicable if you need to do complex integration in your application. For example, a pre token generation trigger, allowing you to customize the claims in the identity token. Another example, a post authentication trigger, allowing you to add custom logic for analytics conversion. Check out more about Lambda Trigger.
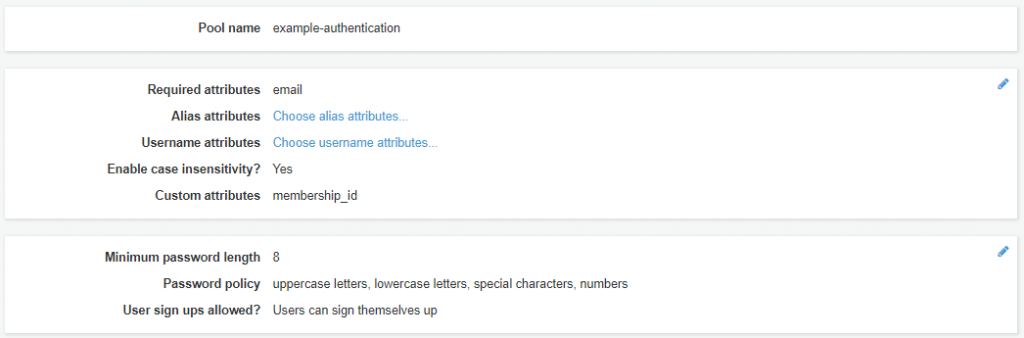
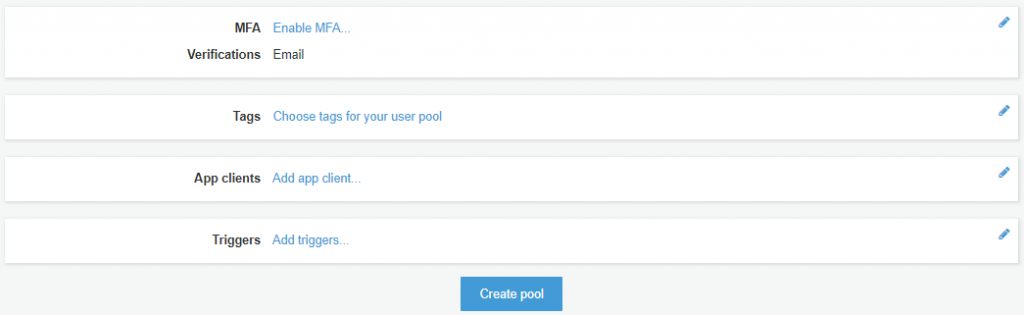
Review
The final step is to review your Cognito User Pool. Once you have confirmed all the configuration, click on the “Create pool” button.
AWS Cognito is a powerful tool for developers. If you are developing an authentication module, then using this service from AWS will save you a lot of coding time.
Moreover, it already supports the integration on many federated identities like Google, Facebook, Apple, Amazon and OpenID. The user can use their existing accounts to sign up or sign in to your application.